Setup Wazuh Central Components※
There is 2 types of components involved in this procedure when it comes to Wazuh, host (central components) and client (agents). I will be starting out with the central components. In my homelab I spun up an Alma Linux VM for this. After doing some basic setup and configuration for the VM itself Its time to install the central components with this command.
curl -sO https://packages.wazuh.com/4.7/wazuh-install.sh && sudo bash ./wazuh-install.sh -a -iOnce the install is complete I get this output, I will be obfuscating my addresses/credentials moving forward.
INFO: --- Summary ---
INFO: You can access the web interface https://<wazuh-dashboard-ip>
User: admin
Password: <ADMIN_PASSWORD>
INFO: Installation finished.Before I try to connect I need to allow port 443 through my firewall
sudo firewall-cmd --zone=public --add-port=443/tcp --permanent
sudo firewall-cmd --reloadI successfully connect to the Wazuh dashboard.
Setup A Wazuh Agent※
From this point we click Add agent and it will take us through a process where we enter various settings so it can tailor us a command to use on the system we want to install the Wazuh agent on.
Here is the command I use to install the agent.
curl -o wazuh-agent-4.7.5-1.x86_64.rpm https://packages.wazuh.com/4.x/yum/wazuh-agent-4.7.5-1.x86_64.rpm && sudo WAZUH_MANAGER='REDACTED' rpm -ihv wazuh-agent-4.7.5-1.x86_64.rpmThen I use this to make sure the services is started up and refreshed.
sudo systemctl daemon-reload
sudo systemctl enable wazuh-agent
sudo systemctl start wazuh-agentNow I check to see if its running properly with a sudo systemctl status wazuh-agent .
? wazuh-agent.service - Wazuh agent
Loaded: loaded (/usr/lib/systemd/system/wazuh-agent.service; enabled; preset: disabled)
Active: active (running) since Thu 2024-06-06 16:04:51 EDT; 8s ago
Process: 186858 ExecStart=/usr/bin/env /var/ossec/bin/wazuh-control start (code=exited, status=0/SUCCESS)
Tasks: 35 (limit: 98980)
Memory: 32.0M
CPU: 355ms
CGroup: /system.slice/wazuh-agent.service
??186885 /var/ossec/bin/wazuh-execd
??186894 /var/ossec/bin/wazuh-agentd
??186908 /var/ossec/bin/wazuh-syscheckd
??186922 /var/ossec/bin/wazuh-logcollector
??186937 /var/ossec/bin/wazuh-modulesd
Jun 06 16:04:46 docker.home.arpa systemd[1]: Starting Wazuh agent...
Jun 06 16:04:46 docker.home.arpa env[186858]: Starting Wazuh v4.7.5...
Jun 06 16:04:46 docker.home.arpa env[186858]: Started wazuh-execd...
Jun 06 16:04:47 docker.home.arpa env[186858]: Started wazuh-agentd...
Jun 06 16:04:48 docker.home.arpa env[186858]: Started wazuh-syscheckd...
Jun 06 16:04:48 docker.home.arpa env[186858]: Started wazuh-logcollector...
Jun 06 16:04:49 docker.home.arpa env[186858]: Started wazuh-modulesd...
Jun 06 16:04:51 docker.home.arpa env[186858]: Completed.
Jun 06 16:04:51 docker.home.arpa systemd[1]: Started Wazuh agent.Now I need to open 2 ports on both the machines, 1514 and 1515 (not sure why but mine likes 1515).
sudo firewall-cmd --zone=public --add-port=1514/tcp --permanent
sudo firewall-cmd --zone=public --add-port=1515/tcp --permanent
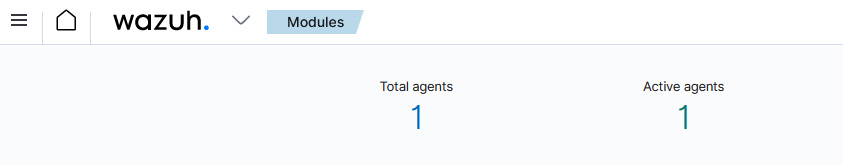
sudo firewall-cmd --reloadNow when I look to the web GUI it is saying there is an agent connected.
Setup Suricata※
I am going to install Suricata on the machine I installed the Wazuh agent on. Then we will tell the Wazuh agent to start relaying data from Suricata to the Wazuh Dashboard for analysis. I will be using Docker to install Suricata this time around. This is the command I use to install Suricata with docker. (I will be using some host bind mounts to expose the logs so the Wazuh agent can see them easily.)
docker run --rm -it --net=host \
--cap-add=net_admin --cap-add=net_raw --cap-add=sys_nice \
-v $(pwd)/logs:/var/log/suricata \
-v $(pwd)/etc:/etc/suricata \
jasonish/suricata:latest -i enp2s0Once its up and running I can test if suricata is working by triggering it and checking the fast.log . Here is the command I used the trigger it and the output in fast.log .
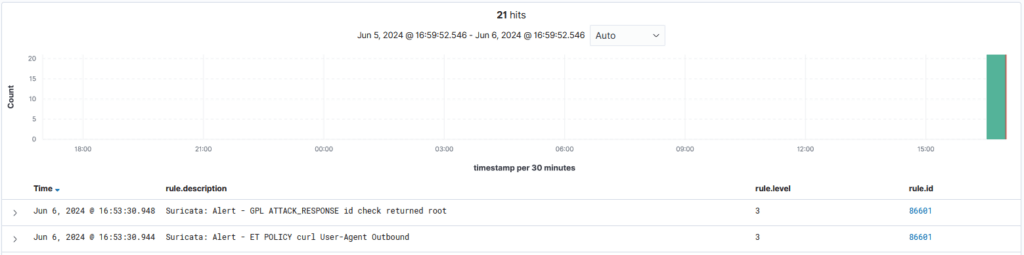
curl http://testmynids.org/uid/index.html06/06/2024-20:45:35.120422 [**] [1:2013028:7] ET POLICY curl User-Agent Outbound [**] [Classification: Attempted Information Leak] [Priority: 2] {TCP} REDACTED -> 65.8.248.33:80
06/06/2024-20:45:35.141577 [**] [1:2100498:7] GPL ATTACK_RESPONSE id check returned root [**] [Classification: Potentially Bad Traffic] [Priority: 2] {TCP} 65.8.248.33:80 -> REDACTEDIntegrating Suricata※
To integrate Suricata its simple I must add this to the ossec.conf on the Wazuh agent machine.
<ossec_config>
<localfile>
<log_format>json</log_format>
<location>/var/log/suricata/eve.json</location>
</localfile>
</ossec_config>When this is done I run my trigger command again for suricata and success! The alert is visible on wazuh.
In conclusion, the integration of Wazuh and Suricata represents a robust and comprehensive approach to enhancing cybersecurity posture. By combining their capabilities, organizations can achieve greater visibility into their IT environments and effectively defend against a wide range of cyber threats. This integration not only strengthens threat detection and incident response capabilities but also streamlines security operations, enabling security teams to proactively identify and mitigate security risks.

